Hello readers,
If you are looking to gain today’s security skills and pass the AZ-500 Microsoft Azure Security Engineer Exam, I have created an in-depth 17+ hrs of AZ-500 Microsoft Azure Security Technologies – AZ-500 Course.
I have covered all the topics that are measured in the exam AZ-500 apart from that the code defense in depth for Azure Cloud Security.
Microsoft technical certifications validate the knowledge, abilities, and skills IT professionals acquire on-the-job and prepare IT professionals to use new technologies. Especially for Securing and Managing Azure cloud. Because IT certifications demonstrate proficiency, certified IT professionals are highly sought-after by companies.
What is Defence in Depth Security ?
When it comes to Defence in depth from AZURE SECURITY, security at the core and provides you built-in controls and tools to meet your security needs. In addition, with machine learning and Microsoft’s significant investments in cyber defense, You can benefit from unique intelligence and proactive measures to protect you from threats. Azure offers unified security management and advanced threat protection for your resources, whether they’re in the cloud, or your data center, or both.
Services in Azure are built with security in mind from the ground up to host your infrastructure, apps, and data. All services are designed and operated to support multiple layers of defense, spanning your data, apps, virtual machines, network, perimeter, related policies, and of course physical security within our data centers. This includes how the data centers and systems that run Azure are architected and operated to the controls you can leverage as part of your defense-in-depth security management. Everything starts with identity and access control.
All Azure resources we’ll mention are governed by Azure Active Directory. Next, one of the most important built-in services to get familiar with is the Azure Security Center.
Across Azure services, it provides unified visibility and control, adaptive threat protection, as well as intelligent threat detection and response. This gives you centralized and real-time monitoring into the security state of your Azure workloads with actionable recommendations and controls.
Azure Security in Depth
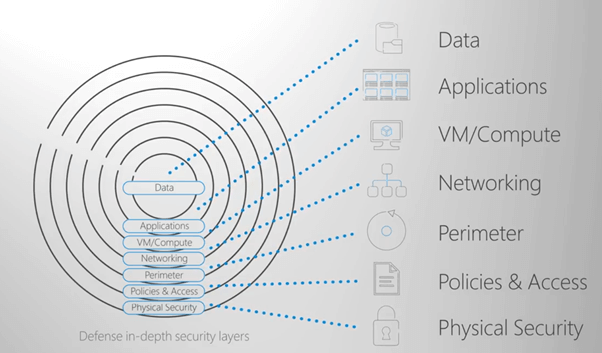
Let’s start with data, which is what you’ll wanna protect the most and is often the core of your apps and services. Data protections are built for both structured and unstructured data. For structured data, all data is encrypted at rest, and machine learning can be used to proactively look for and alert you on potential Security vulnerabilities.
These can be related to data encryption, enabling security telemetry, and extend to capabilities in data services themselves to recommend and enable sensitive information discovery and classification, dynamic data masks to obscure data fields, and more.
Database services in Azure can be configured to run these checks automatically, and Azure’s security center will alert you on any potential issues it finds to keep your data protected. For unstructured data, storage accounts span in blobs, files, tables, and queues are also encrypted at rest, by default, and each account is geo-redundant. You can also apply further protection using access keys to control authentication, shared access signatures for secure delegated access, and granular network firewall controls.
Azure Security Center will report its findings when a security’s at risk, or when protections have been disabled by an admin. Now apps are the front end for accessing and presenting data and their security’s generally governed through data, VMs, or computer platform services in Azure.
Your web apps can be configured to use Azure managed service identities to streamline secure communication with other services connected to Azure AD. You can manage SSL certificates for your apps and even require the clients connecting to your apps have valid certificates for inbound requests.
Now as you move into VMs and compute, the Azure Security Center uses machine learning to continuously access security and vulnerability levels of your VMs, networks, and service configuration.
It also gives your actionable recommendations to prevent exploits before they occur and dynamically applies to allow and block lists to keep out unwanted traffic. As you hope for visibility and control, one thing to know is that many of these capabilities Microsoft gives you also extend to your VMs and other clouds in your data center.
You can also benefit from intelligent threat detection and response. The Security Center leverages a Microsoft Intelligent Security Graph to discover and take action against attacks. The graph combines a cyber intelligence Microsoft collects across all of its services and industry data to block known attack patterns.
Microsoft also gives you the controls that you need to prioritize alerts and incidents that are important to you. In addition, Microsoft gives you a unified view of forensics analysis and the ability to search across all of your computing resources. You can even visualize threat intelligence down to the trending attack techniques and the geographic regions affected.
For network security, the Azure Security Center will assess and report on potential network and security issues related to open ports and firewall settings, and network security groups.
Azure provides additional security when designing and architecting your apps to enforce logical network boundaries and limit permissions to network security groups.
You can also control network and other resources, like VMs, just in time controls for opening management and internet ports, with intelligent recommendations to reduce exposure to brute force attacks. Beyond your network controls, the perimeter security, Azure’s DDoS Protection for protection against Distributed Denial of Service attacks is available at a basic level by default.
Azure’s DDoS Protection Standard Version adds additional protection and mitigations against volumetric attacks, where the attacker’s goal is to flood the network with traffic, in efforts to disable your services. Protocol Attacks where the attackers try to find and exploit weaknesses in layer three and layer four protocol stacks.
Application Layer Attacks, where the web application packets are used to disrupt the transmission of data between hosts, like cross-site scripting or HTTP protocol violations.
For security policies and access management, Azure has a comprehensive set of services to securely manage security policies and access to resources, whether accessed by people or programmatically by your code.
These controls are more than just your front door to who or which processes can access your app’s files or data and extends how granular access is delegated to your IT and development team, using role-based access controls to ensure your team members only have access to what they need.
To automate the response to specific security events, you can also use a security playbook. Powered by Logic App, which is used in Azure to automate workflows, this orchestrates the set of actions that need to happen when a predefined event is detected by the Azure Security Center.
I mentioned earlier, beyond the policies that you can set, security’s infused in everything we do as we develop Azure’s services. From the planning and design phase, all the way to development delivery, using the Secure Development Lifecycle process.
Fabric admins operate Azure’s services with zero standing privilege and use just in time approval processes to gain temporary access to sensitive data or controls when needed.
Azure services compile with both international and industry-specific compliance standards and are subject to rigorous third-party audits that verify Azure Security Controls. So you’ve got peace of mind, especially in answering regulator requirements, such as GDPR.
Finally, Microsoft extends our layered approach to physical security. Data centers managed by Microsoft have extensive layers of protection. Access approval of the facility’s perimeter, the building’s perimeter, inside the building, and on the data center floor.
This layered approach reduces the risk of unauthorized users getting physical access to data on the data center resources. So that was a quick run-through of the primary defense and security considerations in Azure, at every defense-in-depth layer.
These controls are all part of a shared responsibility model in Azure, comprising the security Microsoft manages as the service provider, built-in controls for you to protect your data and infrastructure, and the intelligence Microsoft can provide you from its global scale cyber defense operations.
In conclusion, you can enroll in my course with a discounted coupon attached to this link. In addition, you can go with the below free study guide to learn more about the Azure AZ-500 exam for Security concepts within Azure Cloud.
Skills measured from AZ-500: Microsoft Azure Security Technologies
Manage Identity and Access (20-25%)
Configure Microsoft Azure Active Directory for workloads
Create App Registration, configure App Registration permission scopes, manage App Registration permission consent
- https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-v1-add-azure-ad-app
- https://docs.microsoft.com/en-us/azure/active-directory/develop/v1-permissions-and-consent
- https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-permissions-and-consent
Configure Multi-Factor Authentication settings
Manage Microsoft Azure AD directory groups
Manage Microsoft Azure AD users
Install and configure Microsoft Azure AD Connect, configure authentication methods
- https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-install-custom
- https://docs.microsoft.com/en-us/azure/security/azure-ad-choose-authn
Implement Conditional Access policies
Configure Microsoft Azure AD identity protection
Configure Microsoft Azure AD Privileged Identity Management
Monitor privileged access, configure Access Reviews, activate Privileged Identity Management
- https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-getting-started
- https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-deployment-plan
- https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
Configure Microsoft Azure tenant security
ransfer Microsoft Azure subscriptions between Microsoft Azure AD tenants, manage API access to Microsoft Azure subscriptions and resources
- https://docs.microsoft.com/en-us/azure/billing/billing-subscription-transfer
- https://docs.microsoft.com/en-us/azure/api-management/api-management-howto-aad
- https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-manager-api-authentication
- https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-graph-api
Implement Platform Protection (35-40%)
Implement network security
Configure virtual network connectivity
Configure Network Security Groups (NSGs)
Create and configure Microsoft Azure Firewall
Create and configure application security groups
Configure remote access management
Configure baseline
Configure resource firewall
- https://docs.microsoft.com/en-us/azure/storage/common/storage-network-security
- https://docs.microsoft.com/en-us/azure/sql-database/sql-database-firewall-configure
Implement host security
Configure endpoint security within the VM
Configure VM security
Harden VMs in Microsoft Azure
Configure system updates for VMs in Microsoft Azure
Configure Baseline
Configure container security
Configure network
Configure authentication
Configure container isolation
Configure AKS security
Configure container registry
Configure container instance security
Implement vulnerability management
Implement Microsoft Azure Resource management security
Create Microsoft Azure resource locks
Manage resource group security
Configure Microsoft Azure policies
Configure custom RBAC roles
Configure subscription and resource permissions
Manage Security Operations (15-20%)
Configure security services
Configure Microsoft Azure Monitor
Configure Microsoft Azure Log Analytics
Configure diagnostic logging and log retention
Configure vulnerability scanning
Configure security policies
Configure centralized policy management by using Microsoft Azure Security Center
Configure Just in Time VM access by using Microsoft Azure Security Center
Manage security alerts
Create and customize alerts
Review and respond to alerts and recommendations
- https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
- https://docs.microsoft.com/en-us/azure/security-center/security-center-recommendations
Configure a playbook for a security event by using Microsoft Azure Security Center
Investigate escalated security incidents
Secure Data and Applications (30-35%)
Configure security policies to manage data
Configure data classification
Configure data retention
- https://docs.microsoft.com/en-us/rest/api/storageservices/setting-a-storage-analytics-data-retention-policy
- https://docs.microsoft.com/en-us/azure/kusto/management/retention-policy
Configure data sovereignty
Configure security for data infrastructure
Enable database authentication
Enable database auditing
Configure Microsoft Azure SQL Database threat detection
Configure access control for storage accounts
Configure key management for storage accounts
Create and manage Shared Access Signatures (SAS)
Configure security for HDInsights
Configure security for Cosmos DB
Configure security for Microsoft Azure Data Lake
- https://docs.microsoft.com/en-us/azure/data-lake-store/data-lake-store-network-security
- https://docs.microsoft.com/en-us/azure/storage/common/storage-data-lake-storage-security-guide
Configure encryption for data at rest
Implement Microsoft Azure SQL Database Always Encrypted
Implement database encryption
Implement Storage Service Encryption
Implement disk encryption
Implement backup encryption
Implement security for application delivery
Implement security validations for application development
Configure synthetic security transactions
Configure application security
Configure SSL/TLS certs
Configure Microsoft Azure services to protect web apps
Create an application security baseline
Configure and manage Key Vault (Post: AZ-500 Microsoft Azure Security Engineer Exam)
Manage access to Key Vault
Manage permissions to secrets, certificates, and keys
Manage certificates, manage secrets, configure key rotation
Above all, all the best and thanks for reading this post on AZ-500 Microsoft Azure Security Engineer Exam.
